No. In fact SOC 2 isn’t a legal requirement for anyone. But with that being said SOC 2 is one of the most common compiance frameworks that organizations use to demonstrate security and compliance for protecting customer data.
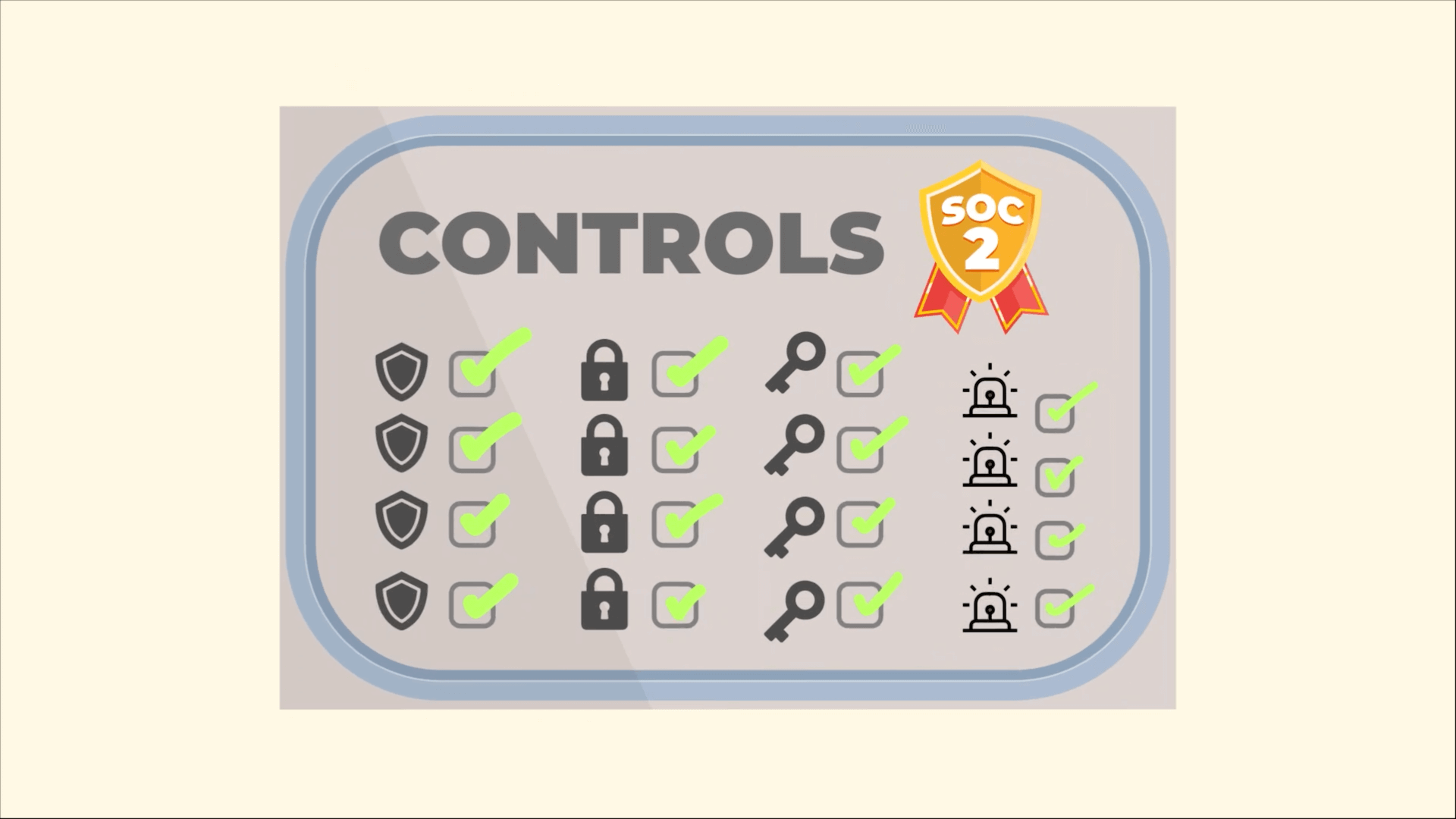
Security is the only required criteria as part of any SOC 2 audit. Below is a summary of the 5 Trust Services Criteria.
1. Security: The security section of a SOC 2 audit examines both the physical and electronic forms of security in use.
2. Availability: Are your customers able to access the system as per contractual specifications?
3. Processing Integrity: If a company offers financial or e-commerce transactions, audit reports should include details on controls designed to safeguard transactions.
4. Confidentiality: Are there any restrictions on how data is shared? Include how data is stored, transferred, and accessed as well as adherence procedures for privacy policies.
5. Privacy: Unlike confidentiality, this area focuses on how your organization collects and uses customer information. Your privacy policy must align with actual operational procedures.
No. While SOC 2 may outline the controls needed, it is up to you and your organization to define what and how those controls operate. There is a lot of flexibility in SOC 2 that your auditor will ask how and why you got to your conclusion to implement those controls. Then they will ensure they are operating as expected.
Yes! Curricula is designed to grow with an organization and its needs starting from Day 1. Our free plan gives every startup the basic necessities to build and launch their first security awareness program effortlessly. Then as your security program matures, we offer additional paid plans that will unlock more content and tools for a mature security awareness program.