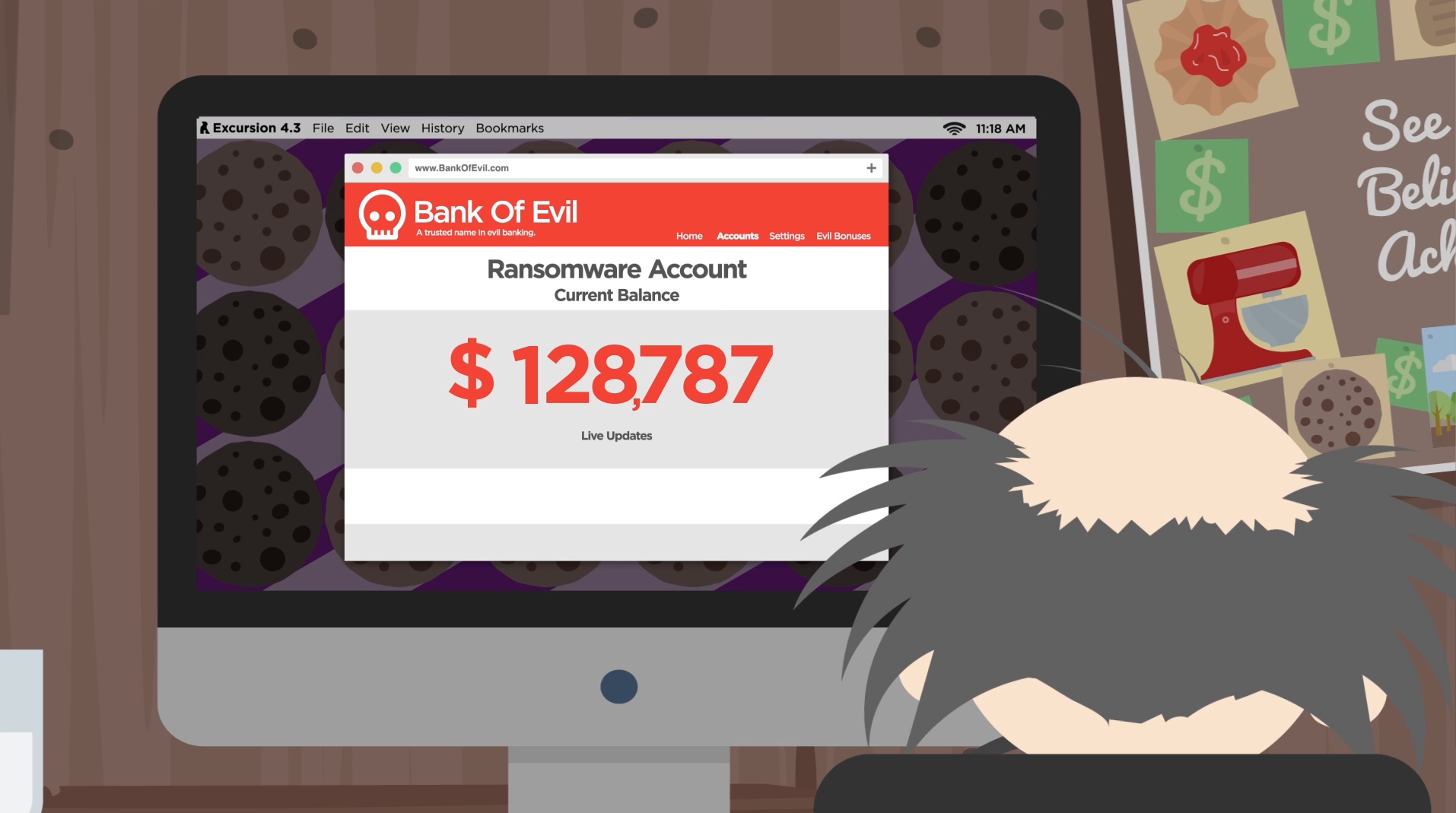
It’s not the first time I’ve seen something like this happen, and it certainly won’t be the last.
During my time as an auditor at the North American Electric Reliability Corporation (NERC) in Critical Infrastructure Protection (CIP), I discussed this topic regularly about how a business IT system can indirectly impact OT (operational technology) systems. The world of industrial control systems is a scary one considering how much we rely on them.
So when I saw the news about Colonial, one of my first thoughts was to reach out to my colleague and cyber expert, Joshua Motta, the CEO and co-founder of Coalition, Inc.Curricula partners with Coalition to provide basic security awareness training to their policyholders for cyber insurance, and we connected for a webinar late last year to discuss the biggest cyber threats in 2021 and beyond.
Joshua has seen it all over the years, and he’s not even 40 (he just made the San Francisco Business Times list of 40 Under 40). He sold his first business to Microsoft at 15, worked as a nation-state adversary for the CIA, and now he’s on a mission at Coalition to help organizations prevent cyber incidents, and assist them with response and recovery in the event of a cyber attack.
We caught up for a chat about what happened to Colonial and how organizations could prevent ransomware
One of the things that stood out to me the most about the Colonial incident was the scope of how ransomware can impact a business through trickling down to other parts of the organization’s infrastructure.
Joshua agreed, reminding us of how everything is interconnected. “We see these ransomware attacks every single day, and it just varies on what’s encrypted plus parts of what they got access to,” he said. “In this case, if it’s billing, you can’t operate a business if you can’t bill your customers.”
While everyone in the security industry—and now the mass media—is talking about how ransomware is getting worse, Joshua said that if you look at the annualized claims data from Coalition policyholders, not much has changed from a claims perspective. But the severity of ransomware has increased as threat actors have become more sophisticated, and we saw the average ransom demand increase 2x from the first half of 2020 through the second half of the year.
“The other part of this equation is severity,” Joshua said. “But the much larger cost is all the other things: the incident response, business interruption, income losses… it’s an open question of how this actually impacted supply, or radically changing demand. Was there actually a shortage of gasoline, or was this the panic from the media frenzy?”

The sky isn’t actually falling. It’s been like this for almost two years now. People are finally taking notice of ransomware because they had to pay a couple of extra bucks to fill their gas tank.
It’s ironic that it was this type of attack that drove this mass awareness of ransomware despite the fact that cyber attacks are an issue that’s been at a pandemic level for a while, Joshua shared. According to what they’ve seen at Coalition, the severity of ransomware attacks peaked in the first half of 2020 and has been decreasing slightly ever since. So essentially the total cost has gone down.
This has been an eye-opener for a lot of people, though, as we’re now looking at how the macroeconomic impact was much bigger since it personally impacted consumers. And it wasn’t because there was a lack of supply of gasoline, but the ensuing panic of people going out of their way to fill up or hoard gas because they did think the sky was falling, thus resulting in the shortage. Remember “toilet-paper-gate” at the beginning of the COVID pandemic?
And this is where I’m starting to think about how major cyber events could impact other industries. These short-term blips on the market ultimately could be caused by something like ransomware.
Take phishing, for example. If an online account is compromised, with the hacker obtaining a user’s password for an account without multi-factor authentication (MFA) enabled, it can ultimately lead to an entire system being shut down.
“These supply chain attacks are super tricky,” Joshua said. “The root cause is poor cyber security hygiene, and unfortunately it’s endemic across the U.S. economy. That’s why companies are being targeted.”
Something that really got my attention was when Joshua shared how these cyber criminals, once they’re inside a system, are largely making a determination to encrypt literally based on whether or not it’s worth their time.
“We have data showing threat actors have lists of companies to target over $1 billion in revenue,” Joshua explained. “There could be someone dormant in your network. A lot of these groups are going big-game hunting.”
Call it what you will, but hackers are essentially creating what we call a target list like account-based marketing to focus on their “prospects” to victimize. Why? Because they know they have money to pay.
At the end of the day, Joshua said that’s their guidance: don’t pay the ransom unless you have to. “What’s worse, paying criminal organizations, rewarding them for criminal behavior, or the survival of a business—particularly small businesses—and those are the ones who might not survive and be entirely disenfranchised?” Joshua opined.
The ransomware business model has evolved. It’s gone from hitting a single computer to an entire business network. It’s gone from not targeting backups to actively targeting backups. It’s gone from just encrypting data to exfiltrating data and threatening the privacy of that data.
In short, every single one of these technological innovations is increasing the leverage that cyber criminals have over their potential victims.
How can basic cyber security hygiene help prevent ransomware?
Joshua and I both agree that most of the attacks we see are not complex in nature. If organizations did some basic cyber hygiene, they can help prevent a devastating attack and at least keep themselves out of the spotlight. Here are some basic recommendations for cyber security best practices to prevent ransomware.
- Security Awareness Training – There is no doubt that some of the highest ROI you can achieve for your cyber security program is security awareness training for all of your employees. This will teach them the basic principles of what to do and what not to do when dealing with today’s modern cyber threats.
- Phishing Simulation Training – As a component of security awareness training, phishing simulation training is designed to practice defending against phishing through real-world tests. These are the best way to simulate what a cyber attack could look like, and to get ahead by proactively educating your employees about how to defend against them.
- Close RDP – Close Remote Desktop Protocol (RDP) on your systems. Just think: if your IT has open RDP connections, a hacker can use those same RDP connections to access your infrastructure.
- Audit yourself – A simple audit of who has access to major bank accounts, procedure review, and basic permissions can be a quick win to make sure you can help prevent a basic oversight.
Curricula and Coalition are here to help
We’re all in this together to educate organizations and their people on cyber security best practices to prevent ransomware. To get started, sign up for a free Coalition Control account and start monitoring your attack surface right away, and also request a free trial of Curricula’s security awareness training.
Ready to watch an Episode?
Try it out for free.